Enabling custom identity broker access to the AWS console
Lets users who sign in to your organization’s identity provider access the AWS Management Console, you can create a custom identity broker:
Architecture and workflow
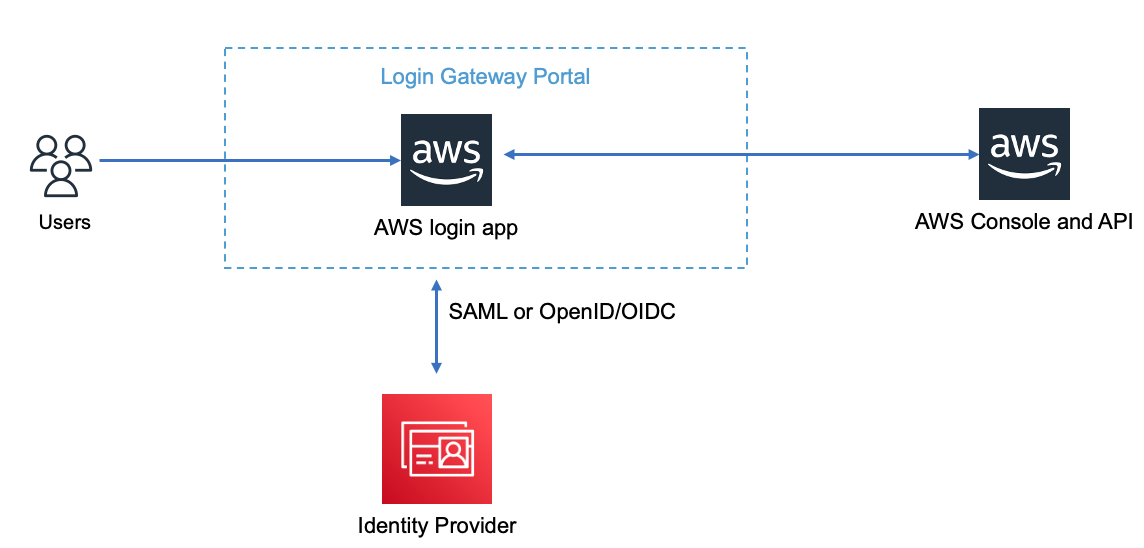
- Users login the Login Gateway Portal
- Login Gateway Portal Manage the Corp Role and AWS IAM Role Mapping
- Login Gateway Portal call AWS API to create temporary security credentials as request a sign-in token (with proper Role permission)
- Login Gateway Portal construct a URL for the console that includes the token.
- User use the URL on the user‘s behalf to access AWS
- User can switch Role from AWS console if user grant multiple AWS IAM Role
The Example using python code logic:
-
Verify that the user is authenticated by your identity provider in your broker application.
-
Call the AWS Security Token Service (AWS STS) AssumeRole to obtain temporary security credentials for the user.
-
Call the AWS federation endpoint and supply the temporary security credentials to request a sign-in token.
-
Construct a URL for the console that includes the token.
-
Give the URL to the user on your broker application or invoke the URL on the user’s behalf.
Follow up Enabling custom identity broker access to the AWS console official guide
Example using python code to construct the URL. The python code need aws profile with permission
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"sts:AssumeRole",
"sts:AssumeRoleWithSAML",
"sts:AssumeRoleWithWebIdentity"
],
"Resource": "*"
}
]
}
6. You can configure the SwitchRole
- Add below permission to the original Role `SSO-ROLE-NAME` grant by AWS STS. The policy allow Role `SSO-ROLE-NAME` switch to Role `TARGET_SWITCH_ROLE_NAME`
```json
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws-cn:iam::ACCOUNT-ID-WITHOUT-HYPHENS:role/TARGET_SWITCH_ROLE_NAME"
}
- Add the Policy to Trusted entities of Role
TARGET_SWITCH_ROLE_NAME. The policy trust RoleSSO-ROLE-NAMESwith to RoleTARGET_SWITCH_ROLE_NAME{ "Effect": "Allow", "Principal": { "AWS": "arn:aws-cn:iam::ACCOUNT-ID-WITHOUT-HYPHENS:role/SSO-ROLE-NAME" }, "Action": "sts:AssumeRole" }