SAML Authentication for Kibana
When you authentication for Kibana, you can
- Authenticating through Amazon Cognito
- Authenticating through the Fine-grained access control internal user database
- SAML authentication for Kibana lets you use your existing identity provider to offer single sign-on (SSO) for Kibana on domains running
Elasticsearch 6.7 or later. To use this feature, you must enablefine-grained access control.
SAML Authentication for Kibana - Active Directory as the identity provider
Follow up the guide: Amazon ElasticSearch SAML Authentication for Kibana
The Kibana login flow can take one of two forms:
-
Service provider (SP) initiated: You navigate to Kibana (for example, https://
/_plugin/kibana), which redirects you to the login screen. After you log in, the identity provider redirects you to Kibana. -
Identity provider (IdP) initiated: You navigate to your identity provider, log in, and choose Kibana from an application directory.
Amazon ES provides two single sign-on URLs, SP-initiated and IdP-initiated, you can choice any of them
- Enabling SAML Authentication
You domain->Actions->Modify authentication->Check Enable SAML authentication.- Note the service provider entity ID and the two SSO URLs, you only need one of the SSO URLs
```bash
Service provider entity ID: https://
IdP-initiated SSO URL: https://
SP-initiated SSO URL: https://
- Configure the Active Directory
- Go to the
ADFS Managementconsole and selectRelying Party Trusts
Right-click on it and select
Add Relying Party Trust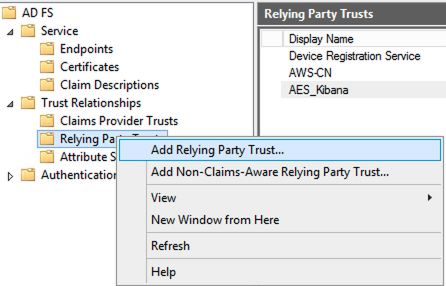
- Go to the
-
Select
Data SourcestepSelect the last option:
Enter data about the relying party manually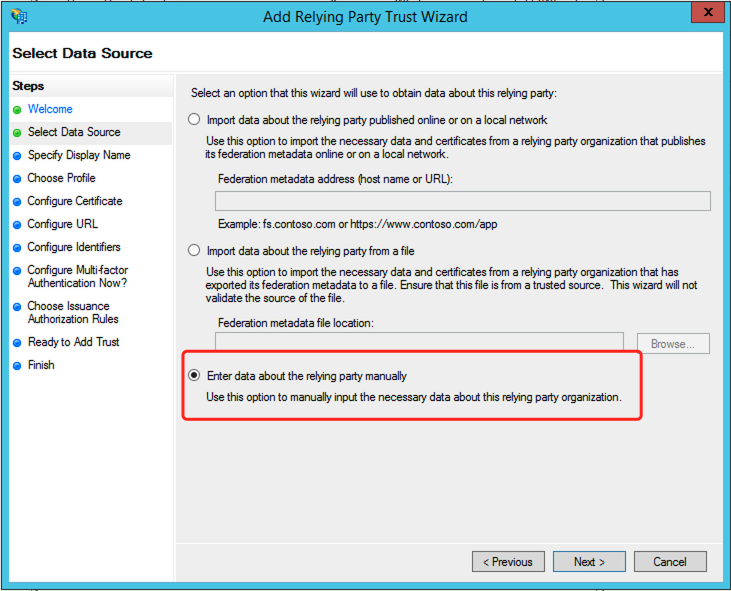
-
Enter a
Display name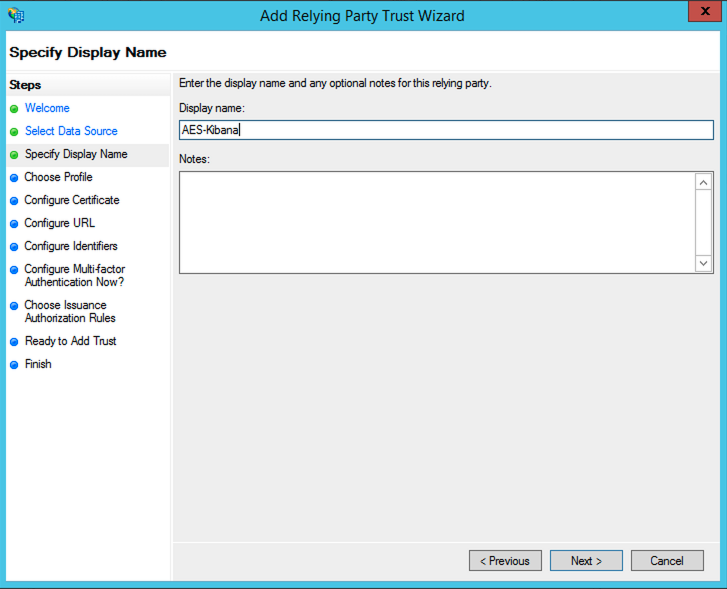
-
Select
AD FS profile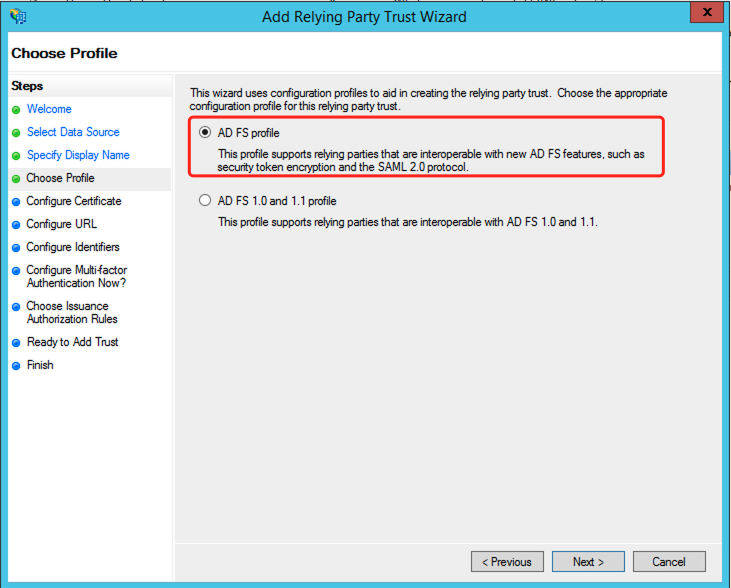
-
Leave the default values for
Configure Certificate
-
Configure URL, selectEnable support for the SAML 2.0 WebSSO protocol.Enter the value of
SP-initiated SSO URLon Kibana console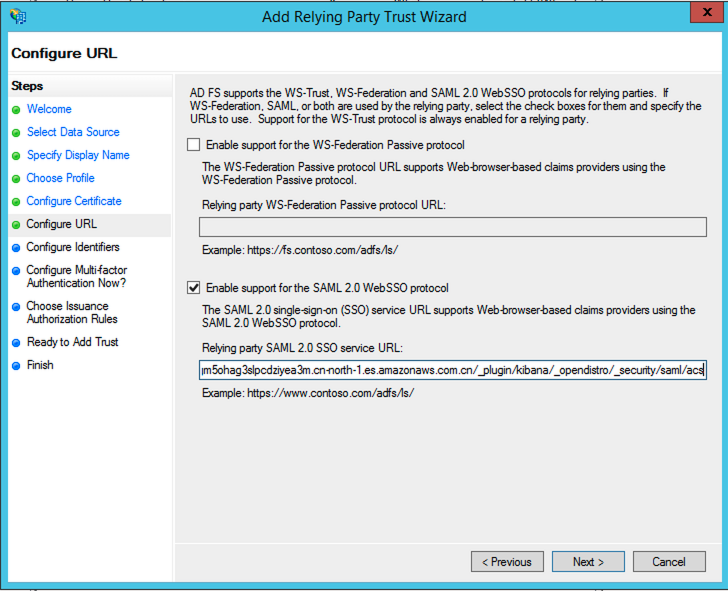
-
Add Relying party trust identifierEnter the value of
Service provider entity IDon Kibana console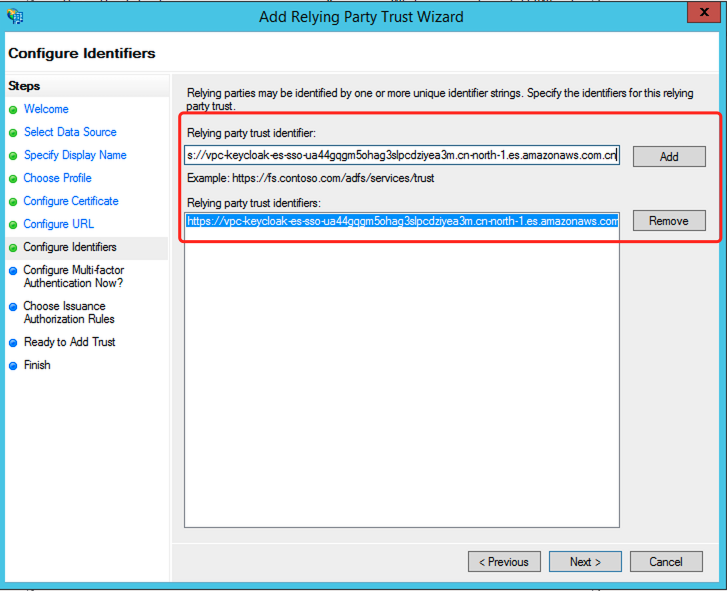
-
Do not enable MFA
-
Next, Choose
Permit all users to access this relying party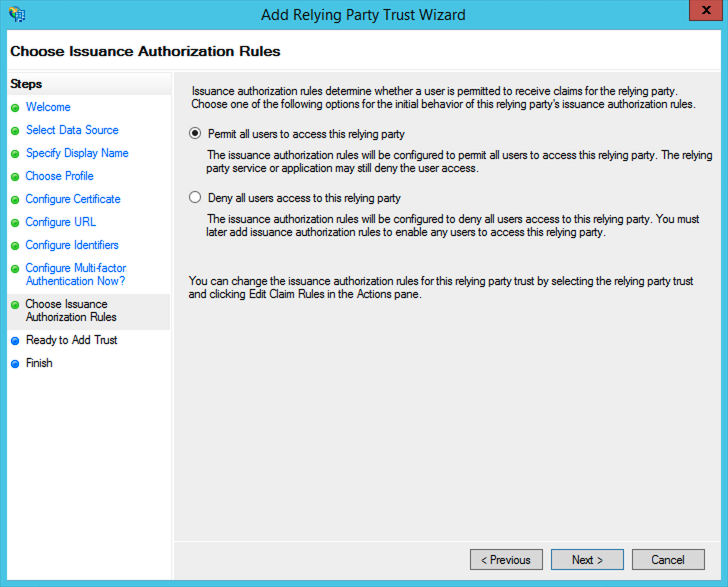
-
Next, Leave the default values
-
On the Final screen
Select
Open the Edit Claim Rules dialogand use theClosebutton to exit.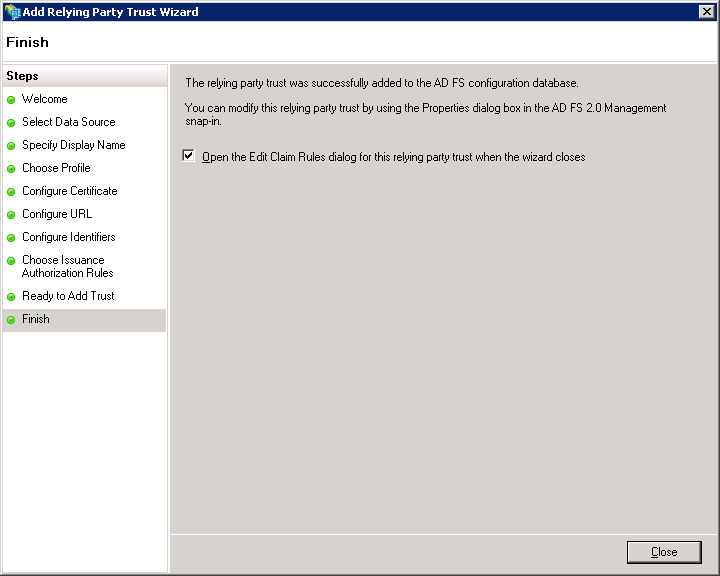
-
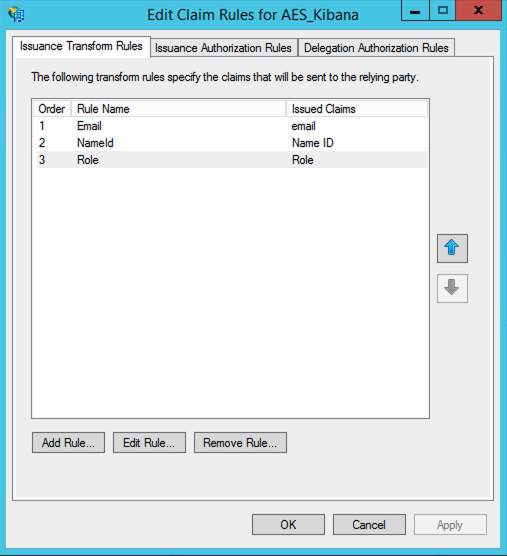
Creating Claims Rules
-
Add the first rule as
Email, SelectSend LDAP Attributes as Claims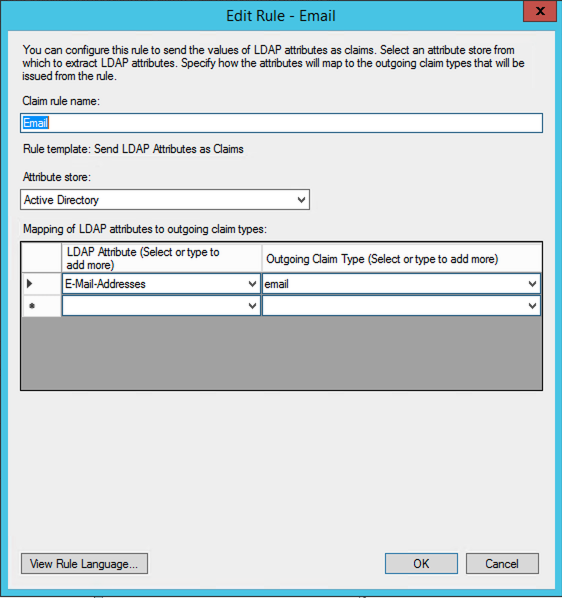
-
Add the second rule as
NameId, SelectTransform an Incoming Claim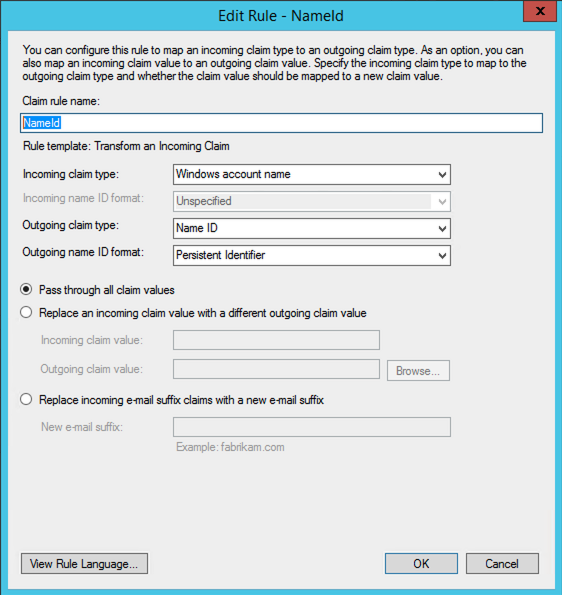
-
Add the third rule as
Role, SelectSend LDAP Attributes as Claims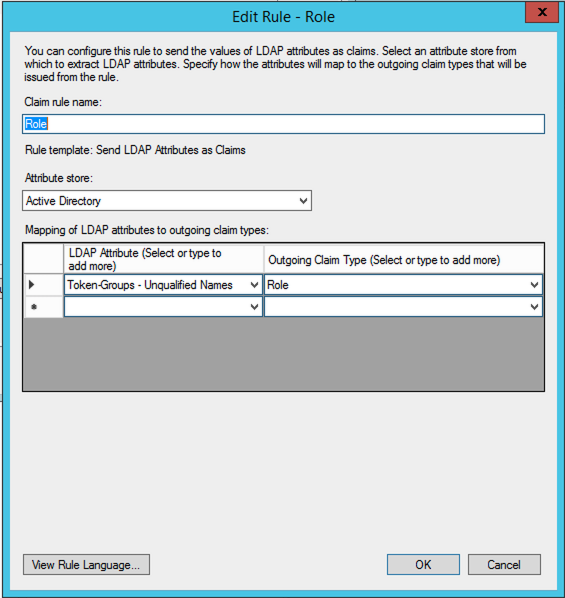
-
Restart Active Directory Federation Service

- Create Active Directory
- Group
ESAdmin - User
esadminuser@tsp.example.combelong toESAdmin - Group
ESRead - Login user
esreader@tsp.example.combelong toESRead
- Group
-
After you configure your identity provider, it generates an IdP metadata file.
Export SAML Metadata Document from https://adfs.tsp.example.com/FederationMetadata/2007-06/FederationMetadata.xml
Import from XML filebutton to importIdP metadata file- Copy and paste the
entityIDproperty from your metadata file into theIDP entity ID -
Provide a
SAML master username(only that user receives full permissions) and/or aSAML master backend role(any user who belongs to the group receives full permissions).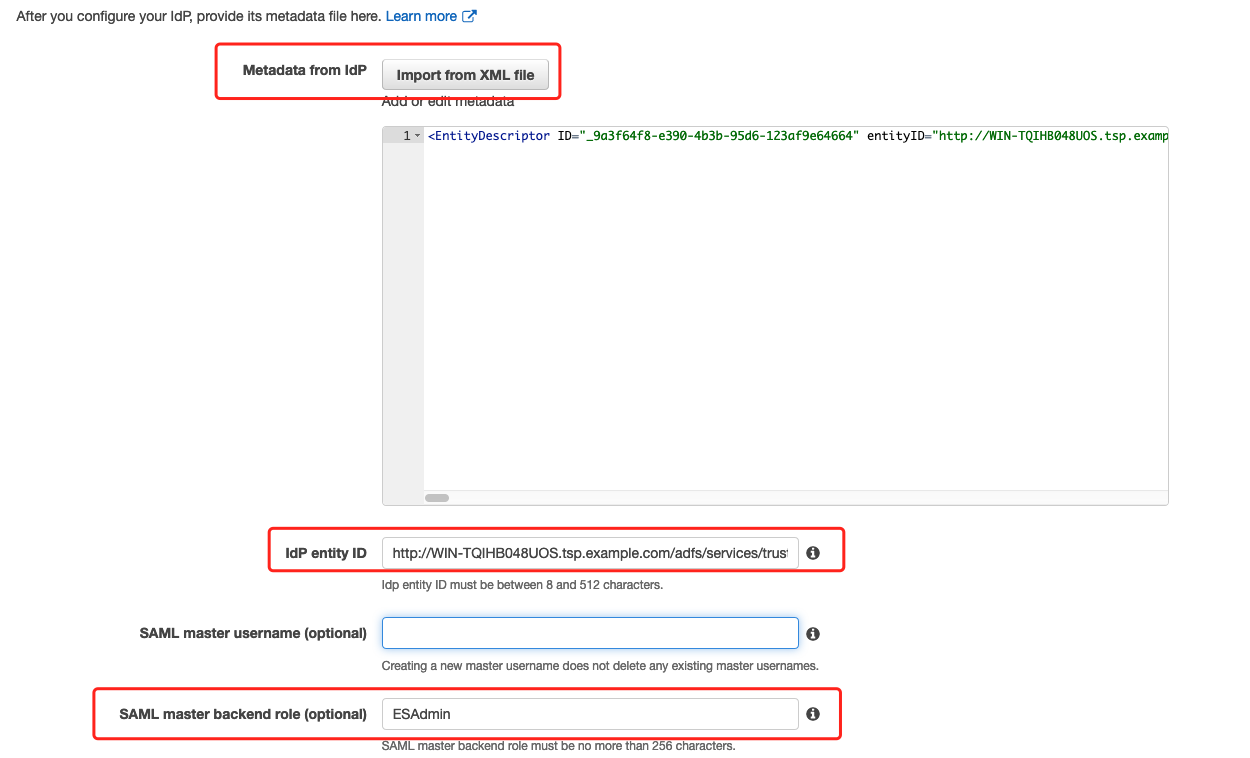
- Leave the
Subject keyfieldemptyto use theNameIDelement of the SAML assertion for the username, you can check the SAML preview to get correctattribute name -
Specify
http://schemas.microsoft.com/ws/2008/06/identity/claims/rolefrom the assertion in theRole keyfield, you can check the SAML preview to get correctattribute name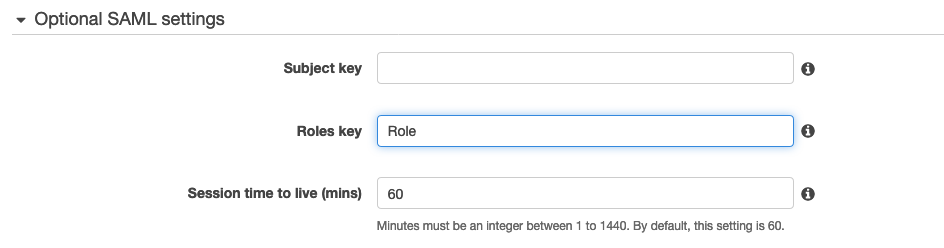
- Choose
Submit. The domain enters aprocessingstate for approximately one minute and change toActivestate
- Access to kibana via https://es-domain/_plugin/kibana, the Active Directory SAML login window will shown up

-
Login user
esadminuser@tsp.example.combelong toESAdmin -
Tips: view a sample assertion during the process, and tools like SAML-tracer
-
A sample of saml assertion get from SAML-tracer
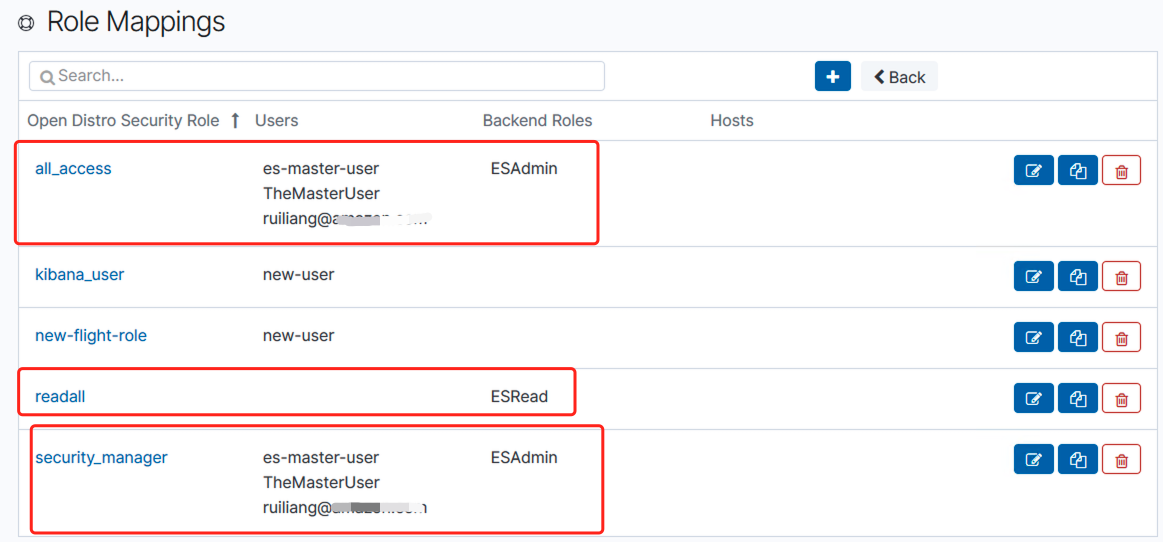
- After Kibana loads, choose
SecurityandRoles.Maproles to allow other users to access Kibana with different permission
- Login user
esreader@tsp.example.combelong toESReadto verify the read only access to the Kibana
Reference
Steps to configure SAML 2.0 SSO with Microsoft Active Directory Federation Services